IO Network
In this document, we will explore the concepts of mesh VPN networks and how we leverage their benefits to improve performance and reliability in the io.net protocol.
IO Network is a cutting-edge networking backend that utilizes a secured mesh VPN to allow ultra-low latency communication between the antMiners nodes 'workers'.
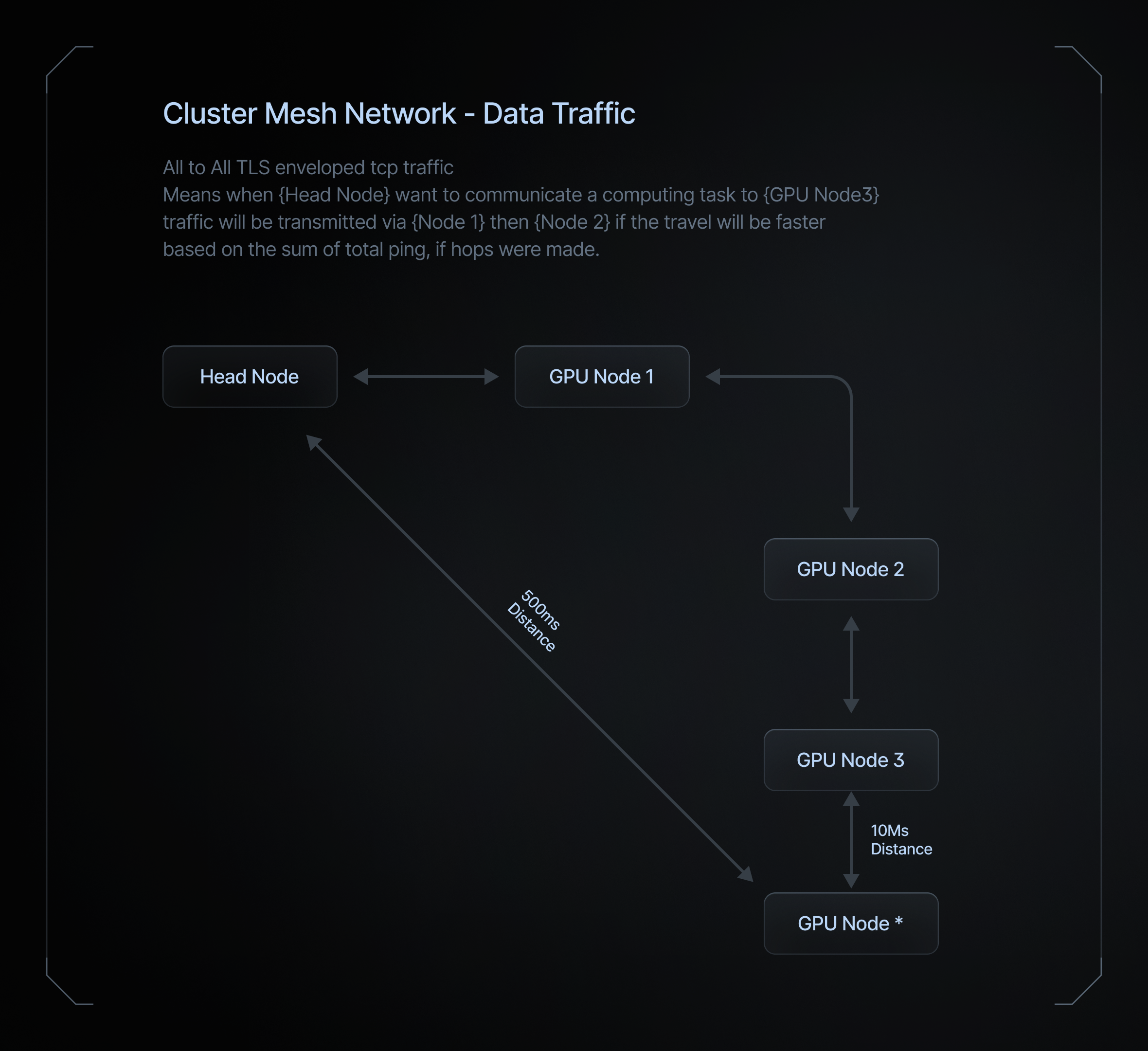
Understanding Mesh VPN Networks
A mesh VPN network is a type of virtual private network (VPN) that connects nodes in a non-hierarchical, decentralized manner. Unlike traditional hub-and-spoke VPN architectures, which rely on a central concentrator or gateway, mesh VPN networks allow each node to connect directly to every other node in the network. This structure ensures data packets can travel along multiple paths, increasing redundancy, fault tolerance, and better load distribution.
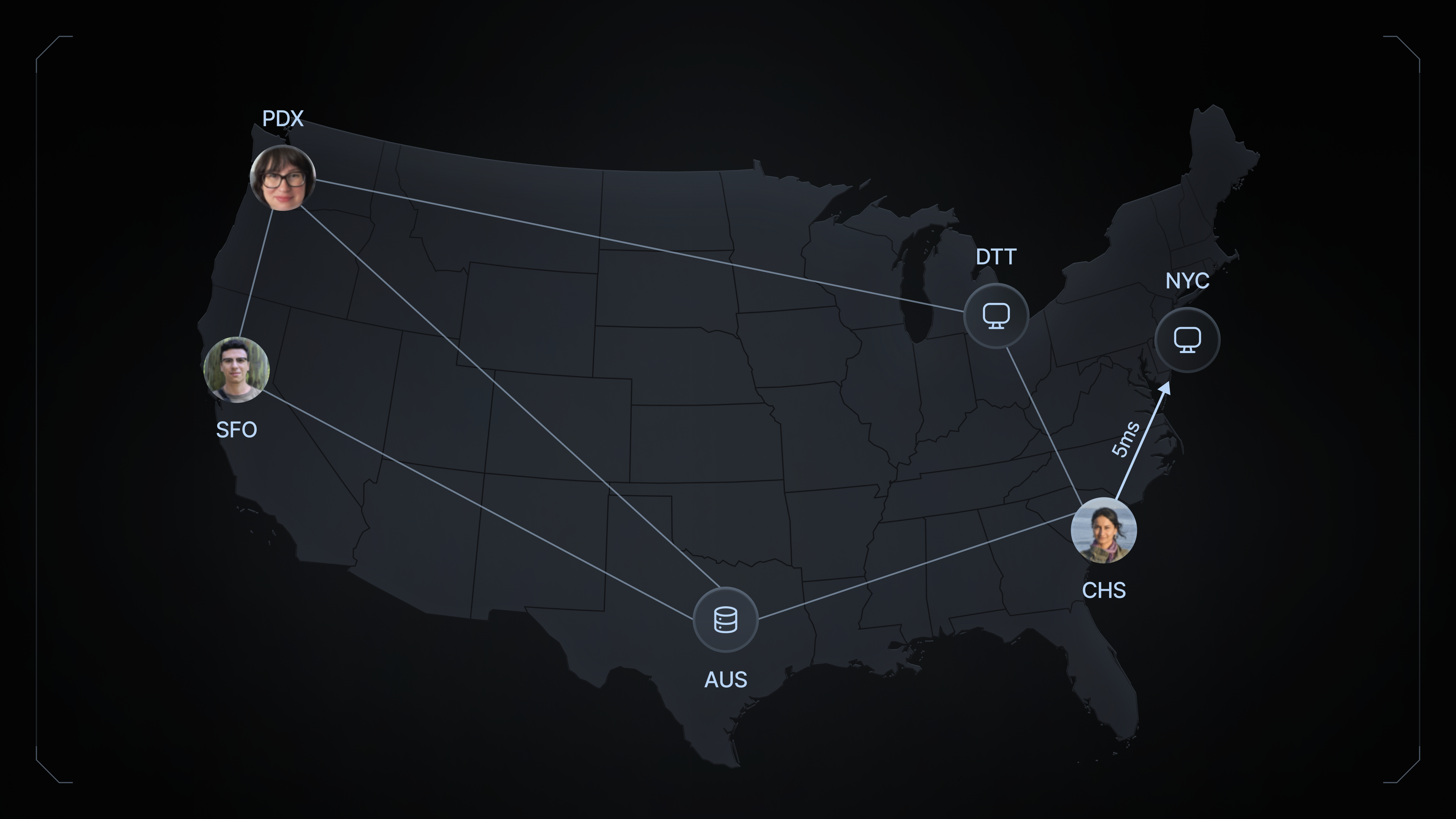
Mesh VPN
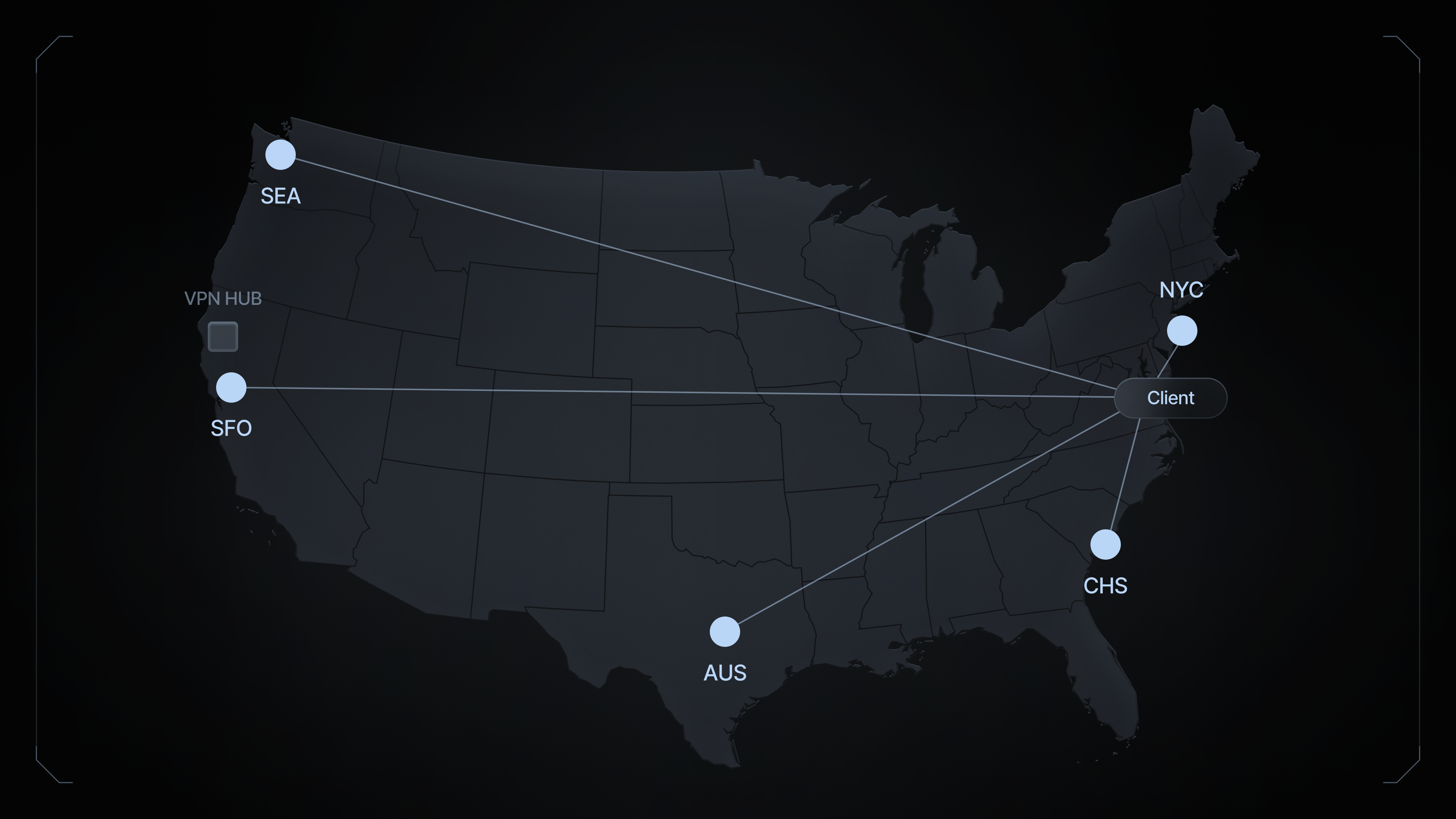
Hub-and-spoke VPN ( legacy - slow )
Advantages of mesh VPN networks include:
- Robust: Mesh networks are resilient to individual node failures, as there are multiple paths for data to travel. This redundancy ensures the network remains operational when one or more nodes experience issues.
- Scalability: Adding new nodes to a mesh network does not significantly impact the overall network performance, making it easy to expand the network as needed.
- Low Latency: By connecting nodes directly, mesh networks reduce the number of hops needed for data to travel between nodes. This reduction in latency enhances the performance of real-time applications and distributed computing.
- Optimized Load Distribution: Mesh networks distribute traffic more evenly across nodes, preventing bottlenecks and ensuring optimal performance.
Implementation of io.net Network
We built an io.net network that creates an efficient, resilient, scalable networking backend. By adopting mesh networking principles, io.net delivers several benefits to its users:
- Enhanced Performance: io.net's mesh network architecture minimizes latency by allowing data to travel along the most efficient paths, optimizing application performance and user experience.
- Improved Resilience: The decentralized nature of io.net's mesh network ensures that it remains operational even when individual nodes fail. This resilience translates to increased reliability and uptime for users.
- Seamless Scalability: io.net's mesh network can easily grow to accommodate more nodes as the user base expands, ensuring consistent performance and adaptability.
- Distributed Computing: By allowing direct connections between nodes, io.net's mesh network facilitates efficient distributed computing, which enables resource sharing and collaborative processing across the network.
Decentralized Architecture and Privacy
The decentralized nature of mesh VPN networks contributes to their security and privacy. Some notable aspects include:
- No Single Points of Failure: The absence of a central concentrator or gateway in mesh VPN networks eliminates the risk of a single point of failure, ensuring that the network remains operational even if individual nodes are compromised or experience issues.
- Anonymity: Since data travels along multiple paths within the mesh network, it becomes more difficult for an attacker to trace the origin or destination of the data, enhancing privacy for users.
- Traffic Obfuscation: Mesh VPN networks can employ techniques like packet padding and timing obfuscation to make it harder for eavesdroppers to analyze traffic patterns and identify specific users or data streams.
Network Access Control and Monitoring
Next for io.net Network is:
- Access Control Lists (ACLs): Nodes should define and enforce ACLs to restrict communication between specific nodes or groups of nodes, ensuring that sensitive data is only accessible to authorized parties and only available during the time they are hired for a specific cluster.
- Regular Auditing and Logging: To maintain security and compliance, the io.net mesh VPN should be configured to allow us to perform regular audits and maintain logs of network activities, enabling administrators to identify and address potential vulnerabilities or breaches.
Updated over 1 year ago
